Leaderboard
Popular Content
Showing content with the highest reputation on 03/20/2024 in all areas
-
3 points
-
2 points
Time Left: 6 years and 7 months
- FOR SALE
- NEW
☢️ Dissecting DEFENSOR: a stealthy Android banking malware #android#apps#malware#mobile Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected. In fact, a blog post released May 22nd 2020 by malware researcher Lukas Stefanko of ESET states, "the banking trojan was available on Google Play at the time of the analysis. The app is fitted with standard information-stealing capabilities; however, this banker is exceptionally insidious in that after installation it requires a single action from the victim – enable Android’s Accessibility Service – to fully unleash the app’s malicious functionality." The blog post also demonstrates at the time of its inception, no antivirus engine detected this malware sample. Even today, only 5-6 detection engines are flagging these two apps, according to VirusTotal. This raises concern for the next iteration of malware that may be nothing but a slight modification of these apps. Android Accessibility Service To make smartphones more accessible to users with special needs, the Accessibility Service allows for the device to extend permissions to an app to read screen content (e.g. for providing text to speech synthesis capability). You can imagine how useful would such a functionality be to a malicious app. Existing detection models can reliably predict when certain combinations of permissions requested by an app may pose problems. But because the Defensor apps mainly relied on obtaining Accessibility Service permissions from the user, along with some other minimalistic ones, no red flags were raised anywhere. The permissions requested by the app include the following, of which the critical ones are highlighted: android.permission.INTERNET android.permission.SYSTEM_ALERT_WINDOW android.permission.BIND_ACCESSIBILITY_SERVICE com.secure.protect.world.permission.C2D_MESSAGE android.permission.ACCESS_NETWORK_STATE android.permission.FOREGROUND_SERVICE android.permission.REQUEST_DELETE_PACKAGES android.permission.SYSTEM_OVERLAY_WINDOW android.permission.WAKE_LOCK android.permission.WRITE_SETTINGS com.google.android.c2dm.permission.RECEIVE In practice, this means the app can capture credentials entered by the user on mobile banking apps, read or generate SMS messages, read emails, read Two-Factor Authentication (2FA) codes generated by authenticator apps — thereby bypassing 2FA, steal cryptocurrency private keys, and so on, and upload all of this vital information to an attacker-controlled server! The app also requests the WAKE_LOCK permission, letting it override the default screen timeout setting, and keeping the device turned on persistently. This would give malware an extended opportunity to launch other apps and to continuously capturing sensitive information. The screenshots provided by ESET demonstrate this behaviour: Indicators of Compromise (IOCs) To make things easy for the security community, malware researchers at ESET have thankfully provided two useful IOCs identifying the malicious apps that have now been yanked from the Google Play store. Package Name SHA-1 Hash SHA-256 Hash ESET detection name com.secure.protect.world F17AEBC741957AA21CFE7C7D7BAEC0900E863F61 BBFB6DEDC01492CA3AC0C4F77343A22162518B306660E9CE958F2A6369FFAF13 Android/Spy.BanBra.A com.brazil.android.free EA069A5C96DC1DB0715923EB68192FD325F3D3CE B5A64791728AA641838D2A478375F5D46F91C91B8DF0CDE34B21DDA2D4D7D8A1 Android/Spy.BanBra.A New information and my analysis ESET researchers have done a brilliant job of presenting their comprehensive analysis of these apps and their documented behaviour. Further to their report however, I'd like to add a bit of my own findings. Command & Control (C&C) domains The attacker controlled C&C domains are still up — well at least one of them, and that's problematic. Domain IP address Task empresasenegocios.online 132.148.42.16 Command & Control (C&C) atendimentoempresarial.digital 184.168.221.46 Command & Control (C&C) The URLs specifically used by the app to establish communication between the attacker-controlled server include: https://empresasenegocios.online/remoteControl/ https://empresasenegocios.online/remoteControl/api/main/index/ http://atendimentoempresarial.digital/remoteControl/api/main/index http://atendimentoempresarial.digital/remoteControl/ Interestingly, VirusTotal reports most antivirus engines are still not flagging these URLs, except for FortiNet which flags just one of the empresasenegocios.online URLs as phishing: Nevermind the fact, the empresasenegocios.online domain still has a fancy admin panel for the attackers to log into and glance over the juicy details of their victims 🍿: Here's also a preview of the API: And the domain continues to be hosted on GoDaddy's shared hosting, with its beautiful cPanel and WebMail interfaces accessible: empresasenegocios.online/cpanel: empresasenegocios.online/webmail: At least, atendimentoempresarial.digital domain has its GoDaddy parking page showing up for now. While that's no guarantee that the domain's malicious ownership or activities have ceased, so far there are no strong signs indicating ongoing activity either. The WHOIS records of these domains didn't reveal anything particularly interesting other than Sãu Paulo, Brazil addresses and phone numbers, which could very likely be fakes, along with two email addresses belonging to the anonymous ProtonMail service: appdados@protonmail.com and notificador@protonmail.com. The Takeaways Enforcing BYOD policies Because prominent antivirus engines are not detecting apps like these — even now, advice to "scan your mobile device" is futile. SOC analysts and Security Ops professionals are strongly advised to enforce a corporate mobile device policy which restricts employee access to Google Play app store on their work devices. Apps like these pose significant threats to an organization's secrets especially when an organization has a relaxed Bring Your Own Device (BYOD) policy, allowing for corporate email accounts to be accessible on an employee's personal mobile device (e.g. Gmail's Android app managing both personal and work accounts of a user would not be immune to attacks like these, and could easily infiltrate corporate trade secrets to malicious actors). Network monitoring and blocks Additionally, extensive network monitoring in your SIEM/EDR products should be setup for these servers, with network blocks implemented, given at least one of these domains is still active. That way, any device on your corporate network would be prevented from inadvertently making calls to these domains. Note: The IP addresses appear to belong to GoDaddy's shared hosting, therefore blocking these could potentially block legitimate websites. It is best to block the malicious domains for the time being. DEFENSOR ID and Defensor Digital were just two of the apps which have been identified and removed from the Play store, but given their stealthy behaviour, we do not know as of yet how many other apps might be using these servers or leveraging the Accessibility Service weakness.$299.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$3,500.00
-
2 points
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
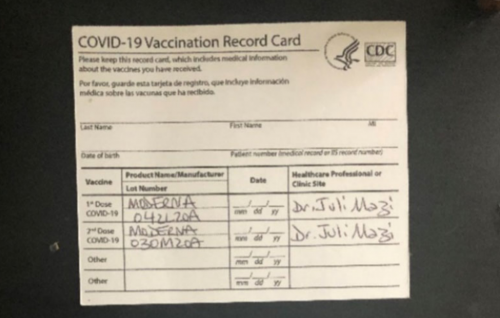
If you need Information on how to obtain Covid-19 Vaccine Cards or information on how to Get a certificate indicating that you’ve been vaccinated, known as the Pass Sanitaire (Covid 19 Sanitary pass) or Pass Vaccinal in France contact us. Get a French/European “covid health pass” , EU or France Certificate, French Vaccine Pass, EU Covid-19 “passport“, covid pass french without the Covid-19 Vaccine with us via our email. We also produce False certificate vaccine of covid or falsified a health pass with QR codes. and we can forward you the information via email after production as digital.$250.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
NFC ATM Jackpotting Malware. Works only at NCR SelfServ NCR ProCash modes (WORLDWIDE). Withdraws all cassettes one-by-one. DOESN'T REQUIRE USB ACCESS OR ANY PHYSICAL INSIDE ACCESS. Injects through NFC card. You will need a very specific software to use it. I'll help with links where you can buy it. Overall spendings will be around 50-100 USD. I will stop selling at any time. As soon as I realize that too many people use it.. Manual and safety guide will be included with software. Any technical details won't be shared until funds are in escrow.$2,000.00
-
1 point
Time Left: 5 years and 8 months
- FOR SALE
- NEW
NEW VERSION AVAILABLE – 2023 version! New Software July,2023 ATM Skimming without any physical contact. This Skimmer will work without a physical connection to ATM/POS Machine. This product is our best-seller, and is most popular credit card skimming device Worldwide. This is GSM data receiver – skimmer. It receives credit card data from ATM`s and POS terminals. Small size 5×4 Centimeters, antenna length 17 centimeters. With one charging it can work up to 8 hours and the manufactured memory can capture about 100000 credit card data, with antenna it can take data in radius of 50 meters. Device can work from (-25 to +45 degrees). We use 3.7V 2500mAh batteries. With one charging the device can work up to 8-10 hours. It have built in a built in memory 32 gb, it can store up to 100000 credit card details with pin codes. Briefly – GSM data receiver is a GSM module receiver which with the help of special software clones and receives all credit card information from ATM`s and POS terminals. The received information is stored by your phone or laptop. To collect this information, you just need to connect the device to your computer or mobile device and the device will send the data to your computer, with the help of the software V22.3.4. GSM receiver have also implemented a new feature, option to add power bank to incase skimming lifetime. GSM data receiver is small & you can easily hide it in your bag, clothes, pocket, or in your car – near the POS/ATM terminal. Device has two led lights – Red and Green Red – Device needs to charge. Flashing red – Device can work for 30 – 40 min more, afterwards it needs to be recharged or added power bank or usb charger. Green+Red – Device is working. Flashing green – Device is connecting. Price for GSM Data Receiver $1000 USD with shipping included. Price for GSM Data Receiver + MSR encoder and 100 pcs cards $1215USD with shipping included.$1,200.00
-
1 point
Time Left: 5 years and 9 months
- FOR SALE
- NEW
The business has been operating for more than 8 years and brings regular profits. Business is 100% online. You can work from anywhere where there is Internet. Employment 2-3 hours a day. There are many options for customer traffic, everyone will find their own, not to the detriment of my business. At the moment, several dozen franchises have been launched, working regularly for profit. The payback period of the business is 1 month. The first client will arrive 7-10 days after the launch. The average check is $800 Max check 12000$ Business is the management of a trading platform - an exchange, and the sale of goods and services on it, the subject of business is specific, I will not specify what kind of goods, otherwise the topic will become public. And now about the most interesting thing, We have learned how to competently pull money out of the client's accounts, while he does not even understand how this happened and it is not possible to convict the organizers of anything. I give you a fishing rod, bring you to a fishing place and teach you how to fish. But you have to catch it, according to my methodology, letting everything take its course means losing. I won't say more about the specifics of the business. Many people have a question about the police? When they hear about illegal business. The police are not interested in this topic at all. Your clients won't even think of going there. Franchise price: The global version has 6 billion customers worldwide. Unlimited traffic flow. with 3 months of work, the profit is $ 10000+ Price 2500$ Next, you can scale (create copies) of your business yourself without asking me anything. Who do I want to see among the franchise buyers: Adequate people with substantive questions. He is polite and friendly with such people. People asking for alms are immediately blacklisted. Required Skills: - Confident use of the computer and the Internet. - The experience of communicating with people (all communication takes place online) And once again for everyone! You are buying a path to a stable online income, not the income itself. You should follow the instructions clearly, and not think that everything will come by itself. I will teach you how to run this business properly, with maximum income. It takes 2-3 days to deploy the project and transfer it to your hands. Then you study my instructions, ask questions and start working. I am always in touch, I will help with advice and business. There is also an option of joint cooperation of our businesses in the future, but only after the purchase.$2,500.00
-
1 point
Time Left: 5 years and 8 months
- FOR SALE
- NEW
SCOTIABANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
Time Left: 5 years and 8 months
- FOR SALE
- NEW
TD BANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
What we offer: they're buying a bitcoin stealer here. this allows you to falsify transactions and send them to your own wallet PSN Genertor + Checker Big Guide for cc to cashout (which is all included: videos, cc to Paypal and much more BTC Stealer Builder 1. PLEASE DO NOT OPEN A DISPUTE WITHOUT NOTIFYING ME !!! 2. DO NOT LEAVE FEEDBACK WITHOUT SENDING ME A MESSAGE (before you complete the order and leave feedback, wait 1-3 days and message me every day. YOU CAN SPAM ME. I'll see sooner if You have a problem problem will be solved) 4. Don't panic if I don't reply to your message within 10 minutes of sending the message. It can take 2-4-6-20 hours for me to reply because I have a lot of work to do 5. DO NOT FINISH THE ORDER WHEN THE ORDER FINALIZES AUTO, DO NOT LEAVE FEEDBACK !!!! SEND me a message because even if the order is complete, I'm here to help !!! 6. If the order is completed automatically, please send me a message. I'm here to help you even after the order is complete 7. DO NOT OPEN A DISPUTE IF YOU HAVE A PROBLEM SEND ME A MESSAGE, YOU WILL GET A FULL REFUND !! 8. Please do not extend the order if the time for the automatic finalization is still more than 1 day. I am here to help 9. Now I offer live support. How does this work? If you need any help redeeming the accounts, please send me a message and we will speak at your requested hours. THANK YOU FOR YOUR UNDERSTANDING !!! If we don't answer immediately, just wait. We'll get in touch the next days at the latest. If a customer leaves positive feedback, he can choose something from our market. If a product doesn't work, don't worry, we're here to solve the problem. We give you a new product and you can get what you want from our shop. You can choose. Refund policy A PRODUCT SHOULD NOT WORK WHAT NATURALLY OCCURS; CAN YOU SEND ME THE EVIDENCE? AND YOU GET A NEW PRODUCT$550.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
Development Notes: Functioning with over 20 Different EMV Writers Used with 1 Encryption code for functionality. Updated frequently to combat Patches from Banks. When banks and other financial institutions introduced chip-based cards, or to be more specific EMV cards, they claimed they were safer. These cards encoded payment information on a microchip. The generation of a one-time use cryptogram further enhanced security of these cards. EMVs were regarded as an upgrade from magstripe cards. And while the world breathed a sigh of relief, believing that their financial transactions were secure, DeepTeam have been busy devising methods to break the barriers of EMV cards. Modern EMV card reader software developed by DeepTeam not only skim data from POS and ATM machines, software can also clone cards. These fake EMV cards are further used to complete cash withdrawals and buy products off the market. The EMV software is one of such EMV reader writer software solutions available on the market. Here’s more on the features of EMV reader-writer software’s and how they work. POS (Point of Sale Machines Compromised) EMV cloning software is designed to read, write, erase, encode and duplicate EMV. In order to complete any of these processes, it requires credit and debit card information that it can copy onto these cards. Thus, the first step is to collect payment card data, often done through using shady means. Scammers compromise point-of-sale systems or ATMs using shimmers. These are unlike the card slot or keypad look-alike fixtures fitted to a sales terminal or ATM. The ‘shimmers’ are paper-thin inserts that fit into the card slot on a point-of-sale terminal. They have an embedded microchip of their own, that steals and stores credit and debit card data every time a person uses their card to make a payment or withdraw cash. The purloined chip data is stored in the device. Again, the skimmers have been updated. While earlier the data skimmer would have to be physically retrieved, modern day skimmer dispenses with it. They are designed to be remotely controlled and transmit data directly via SMS. Dumps The data thus stolen is either used to clone cards or further packaged and sold as dumps to customers. These dumps are used to burn and write cloned cards. Data is stored in the form of tracks on a payment card. The patch helps gather crucial track data needed to complete a transaction such as cardholder name, account number and expiration date. The package also includes access to a tool called “Daphne”(Discontinued) , it records and organizes the credit card information obtained. Cloning Cards An EMV reader writer software allows one to clone and create their own cards that work at almost all point of sale systems. Once connected to the hardware, the EMV card reader software enables multiple functionalities. There are templates for different credit card structures. You can choose from a range of card formats – Visa, MasterCard, Maestro, American Express, Discover and Diners Club. One can also choose between a credit and debit card. The software runs the necessary tests after which the information is transferred to the new card by means of an EMV writer software. The transfer takes place via GPShell script. The new card created is as good as the original. A well-designed user interface makes credit card cloning a breeze. EMV reader writer software is a complete malware suite and makes cloning a hassle free task.$199.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
NFC ATM Jackpotting Malware. Works only at NCR SelfServ NCR ProCash modes (WORLDWIDE). Withdraws all cassettes one-by-one. DOESN'T REQUIRE USB ACCESS OR ANY PHYSICAL INSIDE ACCESS. Injects through NFC card. You will need a very specific software to use it. I'll help with links where you can buy it. Overall spendings will be around 50-100 USD. I will stop selling at any time. As soon as I realize that too many people use it.. Manual and safety guide will be included with software. Any technical details won't be shared until funds are in escrow.$2,200.00
-
1 pointName: Walmart Combo Type: Email Proxies: Yes / No Threads: Yes. Uses Selenium. [align=center][hide] https://www17.zippyshare.com/v/ZLzPLJbB/file.html [/hide][/align] More post coming Soon! Leave a like Rep+ me
-
1 point
-
1 point
-
1 pointEnjoy [hide] fede.cattaneo95@gmail.com:azazel1930 joe33lopez@hotmail.com: serena08 <---(without the space, space bcuz emojis) andreyka_belski@inbox.ru:20022003w profondeum@hotmail.com:Glouille13 rudolphvalentino@hotmail.fr:troopa128 bart.rotjes@home.nl:bartboef1 tylerbutler18@gmail.com:butler40 vallebernava@gmail.com:Messina127 tomogafk007@gmail.com:1998844mmnn gbc79723@gmail.com:z1487561 daniil.lebedev2001@mail.ru:as1as1dani bgmlink@hotmail.com:zeidrian3 alkomlev98@yandex.ru:komlev98 icamps555@gmail.com:GUSANITOCOLITA88 kostik.voronin.00@mail.ru:Juggernaut077 aneno@live.it:Accelo92 afonin.sasha@mail.ru:wolf034687 roartn@gmail.com:0mg0mglol matthew.roberts.94@hotmail.co.uk:Brianna01 littlekangas77@gmail.com:Kangaroo97 luis_oliveir417@hotmail.com:5vc6dpo4 hugo.triep@orange.fr:Hugoipod6 kolya.vysochin@mail.ru:24-05-2002nick yanis.96@live.fr:zefarty72 Beast_ti@mail.ru:A110824rew princess_frosty@hotmail.com:Meggy1221 saintjimmyxd@hotmail.com:masedonia126 [/hide]
-
1 pointits paid mate. hope its really works as expected thank you OP.
-
1 point
-
1 point
-
1 point
-
1 pointUNLOCKED SITES REALITYKINGS MOFOS BABES WICKED REALITY GANG CHANNEL TEEN PINK VIDEOS DAREDORM DIGITALPLAYGROUND BRAZZERS PLAYBOY TV GF REVENGE TWISTYS FAKEHUB TEEN CHANNEL SEXYHUB 3DXSTAR CHANNEL ERITO FITNESS ROOMS FEMALE FAKE TAXI FAKE DRIVING SCHOOL PORNHUB PREMIUM BLACK GFS GF LEAKS PUBLIC PICKUPS I KNOW THAT GIRL DON'T BREAK ME REDTUBE PREMIUM YOUPORN PREMIUM BLACK IS BETTER JAPANS TINIEST [hide] site - https://members.realitykings.com/access/login/ feavtd735:ounwf816 [/hide]
-
1 pointthnx hope it helps a noobie like me
-
1 point
-
1 point
-
1 point
-
1 point[hide]t.j.preperato@gmail.com:mvp4life switherb@gmail.com:pr3siD3nt steven.beckert@gmail.com:oxford42 stephenpham922@gmail.com:random922 [/hide]
-
1 point
-
1 pointi mean why not as if anyone got all the accounts and chanegd rthe pass
-
1 pointYo.. You the man! Always with the clutch on these tools.
-
1 point
-
1 point[align=center][hide] https://www69.zippyshare.com/v/N5APDsdj/file.html [/hide][/align] Leave a Like
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointA database section would be nice for the people who prefer sharing real db instead of combo list
-
1 point
-
1 point






.thumb.jpg.54fe612db4266020538ed9f310d58398.jpg)