Leaderboard
Popular Content
Showing content with the highest reputation on 10/03/2023 in all areas
-
2 points
Time Left: 7 years and 11 months
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$3,500.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
⚠️ WARNING! ALL ITEMS ARE STRICTLY FOR EDUCATIONAL PURPOSES ONLY ;) AT YOUR OWN RISK! INSTANT DELIVERY! ⚠️ 💎 CARDINGS 💎 FRAUDS 💎 EXPLOITS 💎 LEAKS 💎 MALWARES 💎 MEGA AND GIGA PACKS 💎 AND OTHER GOODS! 💎 CHECK MY OTHER LISTINGS! GIVE POSITIVE FEEDBACK TO GET YOUR GIFT! WRITE DM IF FIND ANY ISSUE! Can mine all the following algorithms and thus all the cryptocurrencies that use them, so not only for XMR: cn/upx2, argon2/chukwav2, cn/ccx, kawpow, rx/keva, astrobwt, cn-pico/tlo, rx/sfx, rx/arq, rx/0, argon2/chukwa, argon2/wrkz, rx/wow, cn/fast, cn/rwz, cn/zls, cn/double, cn/r, cn-pico, cn/half, cn/2, cn/xao, cn/rto, cn-heavy/tube, cn-heavy/xhv, cn-heavy/0, cn/1, cn-lite/1, cn-lite/0 and cn/0. 2021 Software! Fast, secure, amazing! Make your own mining network and earn insane money, what you thought impossible! Main Features: - .NET - Coded in Visual Basic .NET, requires .NET Framework 4.5. - Codedom - No need for external libraries to compile - Injection (Silent) - Hide payload behind another process - CPU & GPU Mining - Can mine on Both CPU and GPU (Nvidia & AMD) - Idle Mining - Can be configured to mine with a different Max CPU when computer is idle - Stealth - Pauses the miner while Task Manager, Process Hacker or Process Explorer is open - Watchdog - Replaces the miner if removed and starts it if closed down - Remote Configuration - Can get the connection settings remotely from a URL at each startup - Bypass Windows Defender - Adds exclusions into Windows Defender for the general folders the miner uses - Online Downloader$599.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$2,200.00
-
1 pointAcquired the business a few months ago. I am happy with the purchase, I recaptured the money quickly, found my own way to attract customers)) don't ask, I won't share))
-
1 point
Time Left: 7 years and 11 months
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$3,500.00
-
1 point
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
GSM based (by order available Bluetooth and USB) Available all most popular models like: WINCOR NIXDORF, TRITON, NCR, DIEBOLD Each model comes with PIN pad, also available order separate. Suitable for: USA, Europe, Africa and many other countries. Full kit contains: Pin pad with GSM module inside, cables for charging, rechargeable battery, (all language keyboard available) 3m two side scotch tape to fix skimmer and pin-pad. Skimmer with manufactured GSM module, cables for charging, rechargeable battery. With one charging it can take about 4000 swipes, it depends on the outside temperature. Pin Pad is available in many languages – primary is ENG for more info contact us. MSRV001.V5 Reading head, Smallest Magnetic Reader in the world. With the dimension of 10.4*5.8*2.5mm. USB charger cable CD(software or user manual) Original Factory, welcome any OEM, distributors, resellers, wholesalers. ISO Standard Track 1 210 bpi, 79 Alphanumeric Characters Track 2 75 bpi, 40 Numeric characters Track 3 210 bpi, 107 Numeric characters PRICE: SKIMMER + PIN PAD (OR CAMERA PANEL) starts from $1500 USD WITH SHIPPING INCLUDED. * If you also need MSR reader/writer + 100 blank cards it cost extra 215 USD ** For full orders available discounts.$1,500.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
PAYPAL SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
NATWEST SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
HSBC BANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
DeusEx ATM Jackpot How does it work? I am sending a card that needs to be inserted into the ATM card slot. Or all the data for you to make it yourself. Each subsequent card + 200 $ What is in the manuals? The tools you need, Extra Instructions, Tricks and AV bypass (just in case) How long does the ATM attack take? Depending on small or wall ATM but usually around a Minimum of 3 minutes max 10. Does it work world-wide with all ATM manufacturers? It works world-wide but it does only work with the Wincor Nixdorf and NCR ATMs. Does it bypass the AV? Yes it does, most of the ATMs doesn’t have AVs but there will be a manual include to bypass just in case.$1,200.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
DeusEx ATM Jackpot How does it work? The DeusEx works on the Diebold Nixdorf and NCR ATMs world wide with big wall ATMs and the small ones. You will need to access the ATMs usb ports but they are easy to access, inserts a knife into the faceplate at the top of the ATM, it will flicks out, and exposes the ATMs USB port or drill a hole. There will be manuals included, instructions how it works in detail . Insert the USB stick and press CTRL+ENTER (more in manuals) and a normal Windows Explorer will popup from there browse to the USB stick and open the DeusEx or open cmd and enter the command (E):DeusExATM.exe You will need the following: – Knife or flat screwdriver for small ATMs – Drill with a hole saw/cutter for wall ATMs/(small ATMs) – USB hub (4x ports recommended) – Flashlight – Keyboard with inbuild touchpad or with a separate mouse (wired recommended) – USB Stick with LED (4GB recommended) – The DeusEx malware .exe (SDK just in case) DeusEx ATM Malware [latest] + Full source code – Manuals/Instructions included What is in the manuals? The tools you need, Extra Instructions, Tricks and AV bypass (just in case) How long does the ATM attack take? Depending on small or wall ATM but usually around a Minimum of 3 minutes max 10. Does it work world-wide with all ATM manufacturers? It works world-wide but it does only work with the Wincor Nixdorf and NCR ATMs. Does it bypass the AV? Yes it does, most of the ATMs doesn’t have AVs but there will be a manual include to bypass just in case.$1,000.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
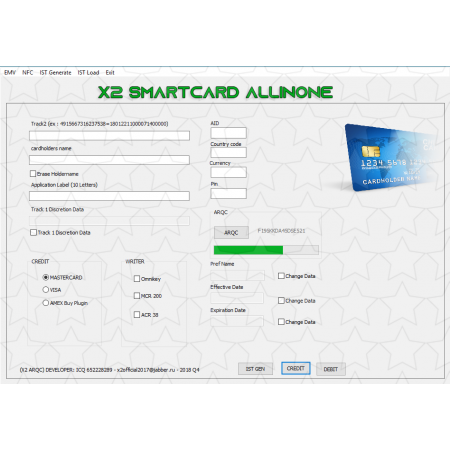
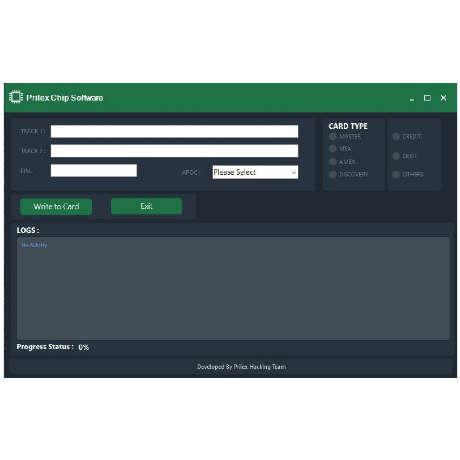
Development Notes: Functioning with over 20 Different EMV Writers Used with 1 Encryption code for functionality. Updated frequently to combat Patches from Banks. When banks and other financial institutions introduced chip-based cards, or to be more specific EMV cards, they claimed they were safer. These cards encoded payment information on a microchip. The generation of a one-time use cryptogram further enhanced security of these cards. EMVs were regarded as an upgrade from magstripe cards. And while the world breathed a sigh of relief, believing that their financial transactions were secure, DeepTeam have been busy devising methods to break the barriers of EMV cards. Modern EMV card reader software developed by DeepTeam not only skim data from POS and ATM machines, software can also clone cards. These fake EMV cards are further used to complete cash withdrawals and buy products off the market. The EMV software is one of such EMV reader writer software solutions available on the market. Here’s more on the features of EMV reader-writer software’s and how they work. POS (Point of Sale Machines Compromised) EMV cloning software is designed to read, write, erase, encode and duplicate EMV. In order to complete any of these processes, it requires credit and debit card information that it can copy onto these cards. Thus, the first step is to collect payment card data, often done through using shady means. Scammers compromise point-of-sale systems or ATMs using shimmers. These are unlike the card slot or keypad look-alike fixtures fitted to a sales terminal or ATM. The ‘shimmers’ are paper-thin inserts that fit into the card slot on a point-of-sale terminal. They have an embedded microchip of their own, that steals and stores credit and debit card data every time a person uses their card to make a payment or withdraw cash. The purloined chip data is stored in the device. Again, the skimmers have been updated. While earlier the data skimmer would have to be physically retrieved, modern day skimmer dispenses with it. They are designed to be remotely controlled and transmit data directly via SMS. Dumps The data thus stolen is either used to clone cards or further packaged and sold as dumps to customers. These dumps are used to burn and write cloned cards. Data is stored in the form of tracks on a payment card. The patch helps gather crucial track data needed to complete a transaction such as cardholder name, account number and expiration date. Cloning Cards An EMV reader writer software allows one to clone and create their own cards that work at almost all point of sale systems. Once connected to the hardware, the EMV card reader software enables multiple functionalities. There are templates for different credit card structures. You can choose from a range of card formats – Visa, MasterCard, Maestro, American Express, Discover and Diners Club. One can also choose between a credit and debit card. The software runs the necessary tests after which the information is transferred to the new card by means of an EMV writer software. The transfer takes place via GPShell script. The new card created is as good as the original. A well-designed user interface makes credit card cloning a breeze. EMV reader writer software is a complete malware suite and makes cloning a hassle free task.$199.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
Development Notes: Functioning with over 20 Different EMV Writers Used with 1 Encryption code for functionality. Updated frequently to combat Patches from Banks. When banks and other financial institutions introduced chip-based cards, or to be more specific EMV cards, they claimed they were safer. These cards encoded payment information on a microchip. The generation of a one-time use cryptogram further enhanced security of these cards. EMVs were regarded as an upgrade from magstripe cards. And while the world breathed a sigh of relief, believing that their financial transactions were secure, DeepTeam have been busy devising methods to break the barriers of EMV cards. Modern EMV card reader software developed by DeepTeam not only skim data from POS and ATM machines, software can also clone cards. These fake EMV cards are further used to complete cash withdrawals and buy products off the market. The EMV software is one of such EMV reader writer software solutions available on the market. Here’s more on the features of EMV reader-writer software’s and how they work. POS (Point of Sale Machines Compromised) EMV cloning software is designed to read, write, erase, encode and duplicate EMV. In order to complete any of these processes, it requires credit and debit card information that it can copy onto these cards. Thus, the first step is to collect payment card data, often done through using shady means. Scammers compromise point-of-sale systems or ATMs using shimmers. These are unlike the card slot or keypad look-alike fixtures fitted to a sales terminal or ATM. The ‘shimmers’ are paper-thin inserts that fit into the card slot on a point-of-sale terminal. They have an embedded microchip of their own, that steals and stores credit and debit card data every time a person uses their card to make a payment or withdraw cash. The purloined chip data is stored in the device. Again, the skimmers have been updated. While earlier the data skimmer would have to be physically retrieved, modern day skimmer dispenses with it. They are designed to be remotely controlled and transmit data directly via SMS. Dumps The data thus stolen is either used to clone cards or further packaged and sold as dumps to customers. These dumps are used to burn and write cloned cards. Data is stored in the form of tracks on a payment card. The patch helps gather crucial track data needed to complete a transaction such as cardholder name, account number and expiration date. The package also includes access to a tool called “Daphne”(Discontinued) , it records and organizes the credit card information obtained. Cloning Cards An EMV reader writer software allows one to clone and create their own cards that work at almost all point of sale systems. Once connected to the hardware, the EMV card reader software enables multiple functionalities. There are templates for different credit card structures. You can choose from a range of card formats – Visa, MasterCard, Maestro, American Express, Discover and Diners Club. One can also choose between a credit and debit card. The software runs the necessary tests after which the information is transferred to the new card by means of an EMV writer software. The transfer takes place via GPShell script. The new card created is as good as the original. A well-designed user interface makes credit card cloning a breeze. EMV reader writer software is a complete malware suite and makes cloning a hassle free task.$199.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
NFC ATM Jackpotting Malware. Works only at NCR SelfServ NCR ProCash modes (WORLDWIDE). Withdraws all cassettes one-by-one. DOESN'T REQUIRE USB ACCESS OR ANY PHYSICAL INSIDE ACCESS. Injects through NFC card. You will need a very specific software to use it. I'll help with links where you can buy it. Overall spendings will be around 50-100 USD. I will stop selling at any time. As soon as I realize that too many people use it.. Manual and safety guide will be included with software. Any technical details won't be shared until funds are in escrow.$2,200.00
-
1 point
-
1 pointProxyRack ($120 plan) < Fine proxies(40$ plan). links be going slow as fuck on proxy rack but i be getting like 200 every minute with fineproxy
-
1 point
-
1 point[align=center]Title: Chipotle Program: BlackBullet. Last Tested: 9/10/2018 Proxies: Default [/align] [hide] Download: Here [/hide]
-
1 pointhow to remove short password line
-
1 point
-
1 point
-
1 point
-
1 pointThanks for this onee
-
1 point
-
1 point
-
1 point[hide] this is a request, thread was moved [/hide] THIS IS NOT CRACKED! THIS IS A REQUEST @CRANK MOVED IT
-
1 point[align=center] Requires Proxies Yes[/align] Recommended: 100 Combo Type Username:Password [align=center]Last Checked: 09/22/2018 CAPTURE: Points, CASH Proof:[/align] [align=center] [hide]https://anonfile.com/19a4Qbh5bf/Points2Shop.com_by_Abdullah346.ini_sccfg[/hide] [/align] YOU KNOW What to do ;)
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointLooks great lets see how this works | thank You
-
1 point
-
1 point
-
1 pointCompromised Data: Username , Hash(MD5) , Email DateofHack: 1 February 2013 Entries: 531k There are 2 files (3 if you consider INFO) , one in this format username:password(MD5):email and the other one email:password(plaintext) [hide]LINK TO DOWNLOAD[/hide]
-
1 pointTitle: Rapidrar Program: BlackBullet. Last Tested: 9/12/2018 Proxies: Yes If you want more you know what to do. Link. [hide]https://anonfile.com/K43fqdhbb0/Rapidrar_ini[/hide]
-
1 point
-
1 pointThanx a lot broo :cry: :cry: Ty for sharing bro
-
1 pointDate of the leak: 09/18/2018 Rows of the combolist: 470,000 Private: Sort of Has been used on websites before the leak: No [hide]http://www.mediafire.com/file/q8a98bpxha7f4n5[/hide] If you want more you know what to do.
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point[align=center] Need a thread design? Minimal logo? Banner?[/align] [align=center]Price starting from 5$ [/align] PM me here or on telegram @boggy94
-
1 point