Leaderboard
Popular Content
Showing content with the highest reputation on 09/02/2023 in all areas
-
3 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
Ncr, Wincor Nixdor, Diebold Insert Skimmer.Full Kit ready for work.Battery can last up to 48 hours,outside temperature doesn’t affect to skimmer working time, because skimmer is located inside ATM.Store up to 15000 credit card tracks. Full Kit Include Insert and remove tools, data cable,software CD, this is plug and play product that is ready for work. Available to order PIN pad as extra option.$1,000.00
-
3 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
GSM based (by order available Bluetooth and USB) Available all most popular models like: WINCOR NIXDORF, TRITON, NCR, DIEBOLD Each model comes with PIN pad, also available order separate. Suitable for: USA, Europe, Africa and many other countries. Full kit contains: Pin pad with GSM module inside, cables for charging, rechargeable battery, (all language keyboard available) 3m two side scotch tape to fix skimmer and pin-pad. Skimmer with manufactured GSM module, cables for charging, rechargeable battery. With one charging it can take about 4000 swipes, it depends on the outside temperature. Pin Pad is available in many languages – primary is ENG for more info contact us. MSRV001.V5 Reading head, Smallest Magnetic Reader in the world. With the dimension of 10.4*5.8*2.5mm. USB charger cable CD(software or user manual) Original Factory, welcome any OEM, distributors, resellers, wholesalers. ISO Standard Track 1 210 bpi, 79 Alphanumeric Characters Track 2 75 bpi, 40 Numeric characters Track 3 210 bpi, 107 Numeric characters PRICE: SKIMMER + PIN PAD (OR CAMERA PANEL) starts from $1500 USD WITH SHIPPING INCLUDED. * If you also need MSR reader/writer + 100 blank cards it cost extra 215 USD ** For full orders available discounts.$1,500.00
-
3 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
SCOTIABANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$2,200.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
UK Identification package (birth certificate,identity card,passport,drivers license) All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$3,000.00
-
2 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
BARCLAYS SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
2 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
NATWEST SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
2 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
UBER SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES.$200.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
DeusEx ATM Jackpot How does it work? I am sending a card that needs to be inserted into the ATM card slot. Or all the data for you to make it yourself. Each subsequent card + 200 $ What is in the manuals? The tools you need, Extra Instructions, Tricks and AV bypass (just in case) How long does the ATM attack take? Depending on small or wall ATM but usually around a Minimum of 3 minutes max 10. Does it work world-wide with all ATM manufacturers? It works world-wide but it does only work with the Wincor Nixdorf and NCR ATMs. Does it bypass the AV? Yes it does, most of the ATMs doesn’t have AVs but there will be a manual include to bypass just in case.$1,200.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
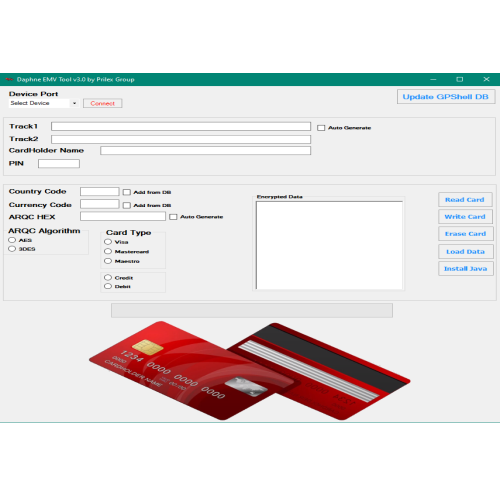
DAPHNE Latest software Because the latest Daphne version 2.0 is rarely supported due to the recent updates in the Security Industry, we come up with a new version of the most known and sophisticated EMV Chip Writer. This time, we gonna be selective with the persons we gonna sell the world’s most up-to-date EMV Chip Software. Anonymity is key here, there must be no leaks to the authorities so only the gentlemen that have the experience needed to operate such powerful software in a quiet manner and that can keep the discretion on theirs and our business will be able to receive Daphne What’s NEW with Daphne EMV Software ? • New improvements to the reclassify ARQC Algorithm. • New improvements to the Java Install on Smart Cards. • New writing methods for SDA & DDA and CDA Chips. • Added new compatibility of EMV Readers / Writers. • Optimized connection with GPShell DB. • The software is faster than ever and can handle multiple tasks. • New bypasser improvements for security level of ATMs & POS Terminals. • Added UpdateSys, that means the software receive automatically updates by our servers, a new version will be no longer neccesary in the future. • We also release new user’s manual with explicit content how to proper use Daphne EMV Software$199.00
-
1 point
-
1 point
Time Left: 6 years and 20 days
- FOR SALE
- NEW
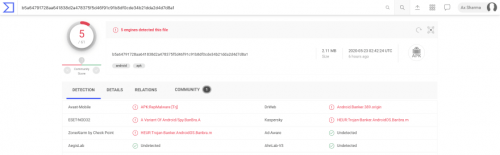
☢️ Dissecting DEFENSOR: a stealthy Android banking malware #android#apps#malware#mobile Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected. In fact, a blog post released May 22nd 2020 by malware researcher Lukas Stefanko of ESET states, "the banking trojan was available on Google Play at the time of the analysis. The app is fitted with standard information-stealing capabilities; however, this banker is exceptionally insidious in that after installation it requires a single action from the victim – enable Android’s Accessibility Service – to fully unleash the app’s malicious functionality." The blog post also demonstrates at the time of its inception, no antivirus engine detected this malware sample. Even today, only 5-6 detection engines are flagging these two apps, according to VirusTotal. This raises concern for the next iteration of malware that may be nothing but a slight modification of these apps. Android Accessibility Service To make smartphones more accessible to users with special needs, the Accessibility Service allows for the device to extend permissions to an app to read screen content (e.g. for providing text to speech synthesis capability). You can imagine how useful would such a functionality be to a malicious app. Existing detection models can reliably predict when certain combinations of permissions requested by an app may pose problems. But because the Defensor apps mainly relied on obtaining Accessibility Service permissions from the user, along with some other minimalistic ones, no red flags were raised anywhere. The permissions requested by the app include the following, of which the critical ones are highlighted: android.permission.INTERNET android.permission.SYSTEM_ALERT_WINDOW android.permission.BIND_ACCESSIBILITY_SERVICE com.secure.protect.world.permission.C2D_MESSAGE android.permission.ACCESS_NETWORK_STATE android.permission.FOREGROUND_SERVICE android.permission.REQUEST_DELETE_PACKAGES android.permission.SYSTEM_OVERLAY_WINDOW android.permission.WAKE_LOCK android.permission.WRITE_SETTINGS com.google.android.c2dm.permission.RECEIVE In practice, this means the app can capture credentials entered by the user on mobile banking apps, read or generate SMS messages, read emails, read Two-Factor Authentication (2FA) codes generated by authenticator apps — thereby bypassing 2FA, steal cryptocurrency private keys, and so on, and upload all of this vital information to an attacker-controlled server! The app also requests the WAKE_LOCK permission, letting it override the default screen timeout setting, and keeping the device turned on persistently. This would give malware an extended opportunity to launch other apps and to continuously capturing sensitive information. The screenshots provided by ESET demonstrate this behaviour: Indicators of Compromise (IOCs) To make things easy for the security community, malware researchers at ESET have thankfully provided two useful IOCs identifying the malicious apps that have now been yanked from the Google Play store. Package Name SHA-1 Hash SHA-256 Hash ESET detection name com.secure.protect.world F17AEBC741957AA21CFE7C7D7BAEC0900E863F61 BBFB6DEDC01492CA3AC0C4F77343A22162518B306660E9CE958F2A6369FFAF13 Android/Spy.BanBra.A com.brazil.android.free EA069A5C96DC1DB0715923EB68192FD325F3D3CE B5A64791728AA641838D2A478375F5D46F91C91B8DF0CDE34B21DDA2D4D7D8A1 Android/Spy.BanBra.A New information and my analysis ESET researchers have done a brilliant job of presenting their comprehensive analysis of these apps and their documented behaviour. Further to their report however, I'd like to add a bit of my own findings. Command & Control (C&C) domains The attacker controlled C&C domains are still up — well at least one of them, and that's problematic. Domain IP address Task empresasenegocios.online 132.148.42.16 Command & Control (C&C) atendimentoempresarial.digital 184.168.221.46 Command & Control (C&C) The URLs specifically used by the app to establish communication between the attacker-controlled server include: https://empresasenegocios.online/remoteControl/ https://empresasenegocios.online/remoteControl/api/main/index/ http://atendimentoempresarial.digital/remoteControl/api/main/index http://atendimentoempresarial.digital/remoteControl/ Interestingly, VirusTotal reports most antivirus engines are still not flagging these URLs, except for FortiNet which flags just one of the empresasenegocios.online URLs as phishing: Nevermind the fact, the empresasenegocios.online domain still has a fancy admin panel for the attackers to log into and glance over the juicy details of their victims 🍿: Here's also a preview of the API: And the domain continues to be hosted on GoDaddy's shared hosting, with its beautiful cPanel and WebMail interfaces accessible: empresasenegocios.online/cpanel: empresasenegocios.online/webmail: At least, atendimentoempresarial.digital domain has its GoDaddy parking page showing up for now. While that's no guarantee that the domain's malicious ownership or activities have ceased, so far there are no strong signs indicating ongoing activity either. The WHOIS records of these domains didn't reveal anything particularly interesting other than Sãu Paulo, Brazil addresses and phone numbers, which could very likely be fakes, along with two email addresses belonging to the anonymous ProtonMail service: appdados@protonmail.com and notificador@protonmail.com. The Takeaways Enforcing BYOD policies Because prominent antivirus engines are not detecting apps like these — even now, advice to "scan your mobile device" is futile. SOC analysts and Security Ops professionals are strongly advised to enforce a corporate mobile device policy which restricts employee access to Google Play app store on their work devices. Apps like these pose significant threats to an organization's secrets especially when an organization has a relaxed Bring Your Own Device (BYOD) policy, allowing for corporate email accounts to be accessible on an employee's personal mobile device (e.g. Gmail's Android app managing both personal and work accounts of a user would not be immune to attacks like these, and could easily infiltrate corporate trade secrets to malicious actors). Network monitoring and blocks Additionally, extensive network monitoring in your SIEM/EDR products should be setup for these servers, with network blocks implemented, given at least one of these domains is still active. That way, any device on your corporate network would be prevented from inadvertently making calls to these domains. Note: The IP addresses appear to belong to GoDaddy's shared hosting, therefore blocking these could potentially block legitimate websites. It is best to block the malicious domains for the time being. DEFENSOR ID and Defensor Digital were just two of the apps which have been identified and removed from the Play store, but given their stealthy behaviour, we do not know as of yet how many other apps might be using these servers or leveraging the Accessibility Service weakness.$299.00
-
1 point
Time Left: 5 years and 3 months
- FOR SALE
- NEW
My team and I will deliver any product from Amazon or Ebay for 40%. The service of receiving parcels by drop is free of charge. You receive the package from us, not from the store. Only you know about the origin of this product, so it is safe. Min. order 250$ ( My share)$250.00
-
1 point
Time Left: 7 years and 11 months
- FOR SALE
- NEW
All our documents are produced on high definition printers. They offer durability, exceptional print quality and an overall impression of quality and authenticity in our real identity pack (birth certificate,identity cards,drivers license passport,sim card ) . We offer a range of features such as barcodes, magnetic stripes, smart chips and holographic overlays. We also offer holographic over laminates, which adds authenticity to the cards. WE ALSO PRODUCE GENUINE DATABASE IDENTIFICATION PACKS FOR OTHER COUNTRIES TOO SO FEEL FREE TO CONTACT US WITH YOUR INQUIRY Refund Policy Refund/Reship policy 100 % refund or Reship Customers who have been loyal will get the best treatment.$3,500.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
HSBC BANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
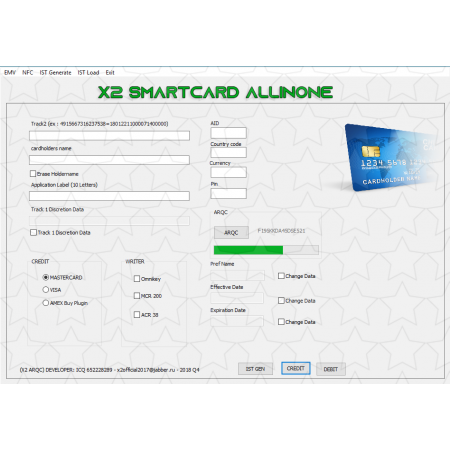
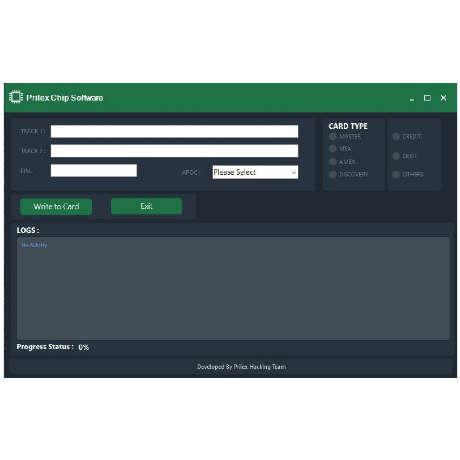
Development Notes: Functioning with over 20 Different EMV Writers Used with 1 Encryption code for functionality. Updated frequently to combat Patches from Banks. When banks and other financial institutions introduced chip-based cards, or to be more specific EMV cards, they claimed they were safer. These cards encoded payment information on a microchip. The generation of a one-time use cryptogram further enhanced security of these cards. EMVs were regarded as an upgrade from magstripe cards. And while the world breathed a sigh of relief, believing that their financial transactions were secure, DeepTeam have been busy devising methods to break the barriers of EMV cards. Modern EMV card reader software developed by DeepTeam not only skim data from POS and ATM machines, software can also clone cards. These fake EMV cards are further used to complete cash withdrawals and buy products off the market. The EMV software is one of such EMV reader writer software solutions available on the market. Here’s more on the features of EMV reader-writer software’s and how they work. POS (Point of Sale Machines Compromised) EMV cloning software is designed to read, write, erase, encode and duplicate EMV. In order to complete any of these processes, it requires credit and debit card information that it can copy onto these cards. Thus, the first step is to collect payment card data, often done through using shady means. Scammers compromise point-of-sale systems or ATMs using shimmers. These are unlike the card slot or keypad look-alike fixtures fitted to a sales terminal or ATM. The ‘shimmers’ are paper-thin inserts that fit into the card slot on a point-of-sale terminal. They have an embedded microchip of their own, that steals and stores credit and debit card data every time a person uses their card to make a payment or withdraw cash. The purloined chip data is stored in the device. Again, the skimmers have been updated. While earlier the data skimmer would have to be physically retrieved, modern day skimmer dispenses with it. They are designed to be remotely controlled and transmit data directly via SMS. Dumps The data thus stolen is either used to clone cards or further packaged and sold as dumps to customers. These dumps are used to burn and write cloned cards. Data is stored in the form of tracks on a payment card. The patch helps gather crucial track data needed to complete a transaction such as cardholder name, account number and expiration date. Cloning Cards An EMV reader writer software allows one to clone and create their own cards that work at almost all point of sale systems. Once connected to the hardware, the EMV card reader software enables multiple functionalities. There are templates for different credit card structures. You can choose from a range of card formats – Visa, MasterCard, Maestro, American Express, Discover and Diners Club. One can also choose between a credit and debit card. The software runs the necessary tests after which the information is transferred to the new card by means of an EMV writer software. The transfer takes place via GPShell script. The new card created is as good as the original. A well-designed user interface makes credit card cloning a breeze. EMV reader writer software is a complete malware suite and makes cloning a hassle free task.$199.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
Development Notes: Functioning with over 20 Different EMV Writers Used with 1 Encryption code for functionality. Updated frequently to combat Patches from Banks. When banks and other financial institutions introduced chip-based cards, or to be more specific EMV cards, they claimed they were safer. These cards encoded payment information on a microchip. The generation of a one-time use cryptogram further enhanced security of these cards. EMVs were regarded as an upgrade from magstripe cards. And while the world breathed a sigh of relief, believing that their financial transactions were secure, DeepTeam have been busy devising methods to break the barriers of EMV cards. Modern EMV card reader software developed by DeepTeam not only skim data from POS and ATM machines, software can also clone cards. These fake EMV cards are further used to complete cash withdrawals and buy products off the market. The EMV software is one of such EMV reader writer software solutions available on the market. Here’s more on the features of EMV reader-writer software’s and how they work. POS (Point of Sale Machines Compromised) EMV cloning software is designed to read, write, erase, encode and duplicate EMV. In order to complete any of these processes, it requires credit and debit card information that it can copy onto these cards. Thus, the first step is to collect payment card data, often done through using shady means. Scammers compromise point-of-sale systems or ATMs using shimmers. These are unlike the card slot or keypad look-alike fixtures fitted to a sales terminal or ATM. The ‘shimmers’ are paper-thin inserts that fit into the card slot on a point-of-sale terminal. They have an embedded microchip of their own, that steals and stores credit and debit card data every time a person uses their card to make a payment or withdraw cash. The purloined chip data is stored in the device. Again, the skimmers have been updated. While earlier the data skimmer would have to be physically retrieved, modern day skimmer dispenses with it. They are designed to be remotely controlled and transmit data directly via SMS. Dumps The data thus stolen is either used to clone cards or further packaged and sold as dumps to customers. These dumps are used to burn and write cloned cards. Data is stored in the form of tracks on a payment card. The patch helps gather crucial track data needed to complete a transaction such as cardholder name, account number and expiration date. The package also includes access to a tool called “Daphne”(Discontinued) , it records and organizes the credit card information obtained. Cloning Cards An EMV reader writer software allows one to clone and create their own cards that work at almost all point of sale systems. Once connected to the hardware, the EMV card reader software enables multiple functionalities. There are templates for different credit card structures. You can choose from a range of card formats – Visa, MasterCard, Maestro, American Express, Discover and Diners Club. One can also choose between a credit and debit card. The software runs the necessary tests after which the information is transferred to the new card by means of an EMV writer software. The transfer takes place via GPShell script. The new card created is as good as the original. A well-designed user interface makes credit card cloning a breeze. EMV reader writer software is a complete malware suite and makes cloning a hassle free task.$199.00
-
1 point219k Premium ComboList part5 [Fortnite,Steam,Origin,Psn,Uplay,Amazon,Spotify,Minecraft,Deezer,Netflix] DOWNLOAD: [hide] https://dropmefiles.com/VOJiT [/hide]
-
1 point
-
1 point
-
1 pointHi lovely crack.sx users, Here you are "Minecraft Checker" Coded by me like a year ago --------------- I use this checker to fastly check my SFAs up or down It cant use proxies so will silentban after 15/20 Accounts You can check your %90 working acccounts without problems --------------- Its source is open,not obfuscated so you can improve add things remove things from it Enjoy ! --------------- It is a .jar file so you need JRE to run it --------------- --------------- Download --------------- [hide] MinecraftAccountChecker-Crack.sx-Nopelcs.jar[/hide]
-
1 point
-
1 pointHi my poor crack.sx friends Im releasing this Guide to help poor guys Who can`t afford Premium Proxy services ----------------------------- This guide will teach you : ❆ How to get proxies daily ❆ How to check proxies with alternative methods ----------------------------- Enjoy them ! Do not leech ----------------------------- [hide] First thing you need is get a proxy checker ❃I use : Proxychecker.zip [This checker also can scrape proxies or you can select your proxy file] [You can select types for scrape or check discover them] ------------------------------------------------------- ------------------------------------------------------- Now we can continue with getting HQ Proxies Hourly Updated Proxies (Socks4,Socks5,HTTP): ❃Free-proxy-list You can select what type proxies you need on page Other alternative places to gather proxies ❃Socks5 : Socks24 - Vipsocks24 ❃HTTPS : SSLProxies24 ❃Mixed US,UK : FreshNewProxies BONUS: Check proxies and scrape them online ❃ CheckerProxy [/hide]
-
1 point
-
1 pointfinally going to used this checker
-
1 point
-
1 pointMade by @Floofs all credit goes to him League of legends checker that has 1. Improved Speeds! (9k CPM with good proxies) 2. Pause/Resume System 3. Increased Speeds on valid password parser 4. New Menu!! 5. Added Support for all proxy types 6. Added Support for all regions [hide] Download : https://www.sendspace.com/file/m3yttv [/hide] Enjoy
-
1 pointWow dude good job, nice work tho :D
-
1 point
-
1 point
-
1 pointedit; its public lol, taken from usermade repo just edited created by antileech, when it was created by bluerar nice job. leecher
-
1 pointgood job, a very good tool, you are the best.
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointthanks thanks brooooooooo
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointI have been waiting for this <3
-
1 point