Leaderboard
Popular Content
Showing content with the highest reputation on 05/24/2023 in all areas
-
4 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
NFC ATM Jackpotting Malware. Works only at NCR SelfServ NCR ProCash modes (WORLDWIDE). Withdraws all cassettes one-by-one. DOESN'T REQUIRE USB ACCESS OR ANY PHYSICAL INSIDE ACCESS. Injects through NFC card. You will need a very specific software to use it. I'll help with links where you can buy it. Overall spendings will be around 50-100 USD. I will stop selling at any time. As soon as I realize that too many people use it.. Manual and safety guide will be included with software. Any technical details won't be shared until funds are in escrow.$2,500.00
-
2 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
NEW VERSION AVAILABLE – 2024 version! New Software July,2023 ATM Skimming without any physical contact. This Skimmer will work without a physical connection to ATM/POS Machine. This product is our best-seller, and is most popular credit card skimming device Worldwide. This is GSM data receiver – skimmer. It receives credit card data from ATM`s and POS terminals. Small size 5×4 Centimeters, antenna length 17 centimeters. With one charging it can work up to 8 hours and the manufactured memory can capture about 100000 credit card data, with antenna it can take data in radius of 50 meters. Device can work from (-25 to +45 degrees). We use 3.7V 2500mAh batteries. With one charging the device can work up to 8-10 hours. It have built in a built in memory 32 gb, it can store up to 100000 credit card details with pin codes. Briefly – GSM data receiver is a GSM module receiver which with the help of special software clones and receives all credit card information from ATM`s and POS terminals. The received information is stored by your phone or laptop. To collect this information, you just need to connect the device to your computer or mobile device and the device will send the data to your computer, with the help of the software V22.3.4. GSM receiver have also implemented a new feature, option to add power bank to incase skimming lifetime. GSM data receiver is small & you can easily hide it in your bag, clothes, pocket, or in your car – near the POS/ATM terminal. Device has two led lights – Red and Green Red – Device needs to charge. Flashing red – Device can work for 30 – 40 min more, afterwards it needs to be recharged or added power bank or usb charger. Green+Red – Device is working. Flashing green – Device is connecting. Price for GSM Data Receiver $1000 USD with shipping included. Price for GSM Data Receiver + MSR encoder and 100 pcs cards $1215USD with shipping included.$1,200.00
-
2 points
Time Left: 5 years and 2 months
- FOR SALE
- NEW
BARCLAYS SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
2 points
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
⚠️ WARNING! ALL ITEMS ARE STRICTLY FOR EDUCATIONAL PURPOSES ONLY ;) AT YOUR OWN RISK! INSTANT DELIVERY! ⚠️ 💎 CARDINGS 💎 FRAUDS 💎 EXPLOITS 💎 LEAKS 💎 MALWARES 💎 MEGA AND GIGA PACKS 💎 AND OTHER GOODS! 💎 CHECK MY OTHER LISTINGS! GIVE POSITIVE FEEDBACK TO GET YOUR GIFT! WRITE DM IF FIND ANY ISSUE! Can mine all the following algorithms and thus all the cryptocurrencies that use them, so not only for XMR: cn/upx2, argon2/chukwav2, cn/ccx, kawpow, rx/keva, astrobwt, cn-pico/tlo, rx/sfx, rx/arq, rx/0, argon2/chukwa, argon2/wrkz, rx/wow, cn/fast, cn/rwz, cn/zls, cn/double, cn/r, cn-pico, cn/half, cn/2, cn/xao, cn/rto, cn-heavy/tube, cn-heavy/xhv, cn-heavy/0, cn/1, cn-lite/1, cn-lite/0 and cn/0. 2021 Software! Fast, secure, amazing! Make your own mining network and earn insane money, what you thought impossible! Main Features: - .NET - Coded in Visual Basic .NET, requires .NET Framework 4.5. - Codedom - No need for external libraries to compile - Injection (Silent) - Hide payload behind another process - CPU & GPU Mining - Can mine on Both CPU and GPU (Nvidia & AMD) - Idle Mining - Can be configured to mine with a different Max CPU when computer is idle - Stealth - Pauses the miner while Task Manager, Process Hacker or Process Explorer is open - Watchdog - Replaces the miner if removed and starts it if closed down - Remote Configuration - Can get the connection settings remotely from a URL at each startup - Bypass Windows Defender - Adds exclusions into Windows Defender for the general folders the miner uses - Online Downloader$599.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
NFC ATM Jackpotting Malware. Works only at NCR SelfServ NCR ProCash modes (WORLDWIDE). Withdraws all cassettes one-by-one. DOESN'T REQUIRE USB ACCESS OR ANY PHYSICAL INSIDE ACCESS. Injects through NFC card. You will need a very specific software to use it. I'll help with links where you can buy it. Overall spendings will be around 50-100 USD. I will stop selling at any time. As soon as I realize that too many people use it.. Manual and safety guide will be included with software. Any technical details won't be shared until funds are in escrow.$2,000.00
-
1 point
Time Left: 6 years and 21 days
- FOR SALE
- NEW
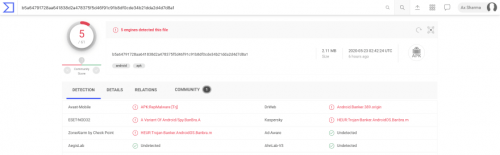
☢️ Dissecting DEFENSOR: a stealthy Android banking malware #android#apps#malware#mobile Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected. In fact, a blog post released May 22nd 2020 by malware researcher Lukas Stefanko of ESET states, "the banking trojan was available on Google Play at the time of the analysis. The app is fitted with standard information-stealing capabilities; however, this banker is exceptionally insidious in that after installation it requires a single action from the victim – enable Android’s Accessibility Service – to fully unleash the app’s malicious functionality." The blog post also demonstrates at the time of its inception, no antivirus engine detected this malware sample. Even today, only 5-6 detection engines are flagging these two apps, according to VirusTotal. This raises concern for the next iteration of malware that may be nothing but a slight modification of these apps. Android Accessibility Service To make smartphones more accessible to users with special needs, the Accessibility Service allows for the device to extend permissions to an app to read screen content (e.g. for providing text to speech synthesis capability). You can imagine how useful would such a functionality be to a malicious app. Existing detection models can reliably predict when certain combinations of permissions requested by an app may pose problems. But because the Defensor apps mainly relied on obtaining Accessibility Service permissions from the user, along with some other minimalistic ones, no red flags were raised anywhere. The permissions requested by the app include the following, of which the critical ones are highlighted: android.permission.INTERNET android.permission.SYSTEM_ALERT_WINDOW android.permission.BIND_ACCESSIBILITY_SERVICE com.secure.protect.world.permission.C2D_MESSAGE android.permission.ACCESS_NETWORK_STATE android.permission.FOREGROUND_SERVICE android.permission.REQUEST_DELETE_PACKAGES android.permission.SYSTEM_OVERLAY_WINDOW android.permission.WAKE_LOCK android.permission.WRITE_SETTINGS com.google.android.c2dm.permission.RECEIVE In practice, this means the app can capture credentials entered by the user on mobile banking apps, read or generate SMS messages, read emails, read Two-Factor Authentication (2FA) codes generated by authenticator apps — thereby bypassing 2FA, steal cryptocurrency private keys, and so on, and upload all of this vital information to an attacker-controlled server! The app also requests the WAKE_LOCK permission, letting it override the default screen timeout setting, and keeping the device turned on persistently. This would give malware an extended opportunity to launch other apps and to continuously capturing sensitive information. The screenshots provided by ESET demonstrate this behaviour: Indicators of Compromise (IOCs) To make things easy for the security community, malware researchers at ESET have thankfully provided two useful IOCs identifying the malicious apps that have now been yanked from the Google Play store. Package Name SHA-1 Hash SHA-256 Hash ESET detection name com.secure.protect.world F17AEBC741957AA21CFE7C7D7BAEC0900E863F61 BBFB6DEDC01492CA3AC0C4F77343A22162518B306660E9CE958F2A6369FFAF13 Android/Spy.BanBra.A com.brazil.android.free EA069A5C96DC1DB0715923EB68192FD325F3D3CE B5A64791728AA641838D2A478375F5D46F91C91B8DF0CDE34B21DDA2D4D7D8A1 Android/Spy.BanBra.A New information and my analysis ESET researchers have done a brilliant job of presenting their comprehensive analysis of these apps and their documented behaviour. Further to their report however, I'd like to add a bit of my own findings. Command & Control (C&C) domains The attacker controlled C&C domains are still up — well at least one of them, and that's problematic. Domain IP address Task empresasenegocios.online 132.148.42.16 Command & Control (C&C) atendimentoempresarial.digital 184.168.221.46 Command & Control (C&C) The URLs specifically used by the app to establish communication between the attacker-controlled server include: https://empresasenegocios.online/remoteControl/ https://empresasenegocios.online/remoteControl/api/main/index/ http://atendimentoempresarial.digital/remoteControl/api/main/index http://atendimentoempresarial.digital/remoteControl/ Interestingly, VirusTotal reports most antivirus engines are still not flagging these URLs, except for FortiNet which flags just one of the empresasenegocios.online URLs as phishing: Nevermind the fact, the empresasenegocios.online domain still has a fancy admin panel for the attackers to log into and glance over the juicy details of their victims 🍿: Here's also a preview of the API: And the domain continues to be hosted on GoDaddy's shared hosting, with its beautiful cPanel and WebMail interfaces accessible: empresasenegocios.online/cpanel: empresasenegocios.online/webmail: At least, atendimentoempresarial.digital domain has its GoDaddy parking page showing up for now. While that's no guarantee that the domain's malicious ownership or activities have ceased, so far there are no strong signs indicating ongoing activity either. The WHOIS records of these domains didn't reveal anything particularly interesting other than Sãu Paulo, Brazil addresses and phone numbers, which could very likely be fakes, along with two email addresses belonging to the anonymous ProtonMail service: appdados@protonmail.com and notificador@protonmail.com. The Takeaways Enforcing BYOD policies Because prominent antivirus engines are not detecting apps like these — even now, advice to "scan your mobile device" is futile. SOC analysts and Security Ops professionals are strongly advised to enforce a corporate mobile device policy which restricts employee access to Google Play app store on their work devices. Apps like these pose significant threats to an organization's secrets especially when an organization has a relaxed Bring Your Own Device (BYOD) policy, allowing for corporate email accounts to be accessible on an employee's personal mobile device (e.g. Gmail's Android app managing both personal and work accounts of a user would not be immune to attacks like these, and could easily infiltrate corporate trade secrets to malicious actors). Network monitoring and blocks Additionally, extensive network monitoring in your SIEM/EDR products should be setup for these servers, with network blocks implemented, given at least one of these domains is still active. That way, any device on your corporate network would be prevented from inadvertently making calls to these domains. Note: The IP addresses appear to belong to GoDaddy's shared hosting, therefore blocking these could potentially block legitimate websites. It is best to block the malicious domains for the time being. DEFENSOR ID and Defensor Digital were just two of the apps which have been identified and removed from the Play store, but given their stealthy behaviour, we do not know as of yet how many other apps might be using these servers or leveraging the Accessibility Service weakness.$299.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
Ncr, Wincor Nixdor, Diebold Insert Skimmer.Full Kit ready for work.Battery can last up to 48 hours,outside temperature doesn’t affect to skimmer working time, because skimmer is located inside ATM.Store up to 15000 credit card tracks. Full Kit Include Insert and remove tools, data cable,software CD, this is plug and play product that is ready for work. Available to order PIN pad as extra option.$1,000.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
GSM based (by order available Bluetooth and USB) Available all most popular models like: WINCOR NIXDORF, TRITON, NCR, DIEBOLD Each model comes with PIN pad, also available order separate. Suitable for: USA, Europe, Africa and many other countries. Full kit contains: Pin pad with GSM module inside, cables for charging, rechargeable battery, (all language keyboard available) 3m two side scotch tape to fix skimmer and pin-pad. Skimmer with manufactured GSM module, cables for charging, rechargeable battery. With one charging it can take about 4000 swipes, it depends on the outside temperature. Pin Pad is available in many languages – primary is ENG for more info contact us. MSRV001.V5 Reading head, Smallest Magnetic Reader in the world. With the dimension of 10.4*5.8*2.5mm. USB charger cable CD(software or user manual) Original Factory, welcome any OEM, distributors, resellers, wholesalers. ISO Standard Track 1 210 bpi, 79 Alphanumeric Characters Track 2 75 bpi, 40 Numeric characters Track 3 210 bpi, 107 Numeric characters PRICE: SKIMMER + PIN PAD (OR CAMERA PANEL) starts from $1500 USD WITH SHIPPING INCLUDED. * If you also need MSR reader/writer + 100 blank cards it cost extra 215 USD ** For full orders available discounts.$1,500.00
-
1 point
Time Left: 5 years and 2 months
- FOR SALE
- NEW
LLOYDS BANK SCAMPAGE .ZIP FILES UPLOAD AND UNZIP EDIT NECESSARY FILES WITH SOFTWARE OR ON SERVER UNDETECTABLE TO MANY SERVER INSTAT DELIVERY PLEASE CONTACT ME IF MORE HELP IS REQUIRED FOR ANY PRODUCT. DO NOT DISPUTE AN ORDER THE ADMIN IS VERY BUSY AND THEY WILL TAKE FOREVER TO SOLVE YOUR EMOTION ISSUES$200.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
Description IMPORTANT! -100% Guarantee! IMPORTANT! -Instant Delivery! IMPORTANT! -Request your bonus after positive feedback! Item description: About me: I am a carder myself with more than 10 years of experience! With the Cashout Methods I am using myself and now offering to you guys you can easily make up to 4000 - 6000 $/£ per DAY Easily! All methods are based on my own experiences. Again: I am using all methods by myself and they work 100 You can make thousands of dollars/Pounds every single day when mastering these methods Some methods are so simple you can't do anything wrong!!! I promise! You will get: - 5 proven step-by-step CASHOUT METHODS that are working 100% (All up to date - 2021! n easy to follow even for BEGINNER) - list of legit darkweb CVV VENDORS I am using myself (Never get scammed again!) - list of CARDABLE SITES (Never kill card due to high security level of website!) Once ordered you will get a download link with PDF Guide which contains all information mentioned above Refund policy Please Give Me Enough Time To Reply To You Before You Leave A Review (If You Have A Problem) Kind Regards$229.00
-
1 point
THIS ADVERT HAS EXPIRED!
- FOR SALE
- NEW
This contains 13 really great methods to make a great living with carding. Besides different websites and techniques this are the highlights in the guides: - Top notch carding video's and pdfs - Anonimity, changing socks5 and top socks5 providers - The best way to connect RDP - Cashing out CC in front of YOU, making $250 in 15 minutes - CARDING SAMSUNG phones - Cashing out PAYPAL accounts$499.00
-
1 point219k Premium ComboList part5 [Fortnite,Steam,Origin,Psn,Uplay,Amazon,Spotify,Minecraft,Deezer,Netflix] DOWNLOAD: [hide] https://dropmefiles.com/VOJiT [/hide]
-
1 point
-
1 pointI am offering a configs service. I can create configs for Storm , Snipr, Sentry and Black Bullet full with capture. Can create configs for Both Website/Mobile APPS Can fix your broken configs or update them with relevent criteria Price Ranges: 8$-30$ depends on what you are looking for or the difficulty of site. Want to Purchase? Use this Format to send me details [align=center] [code] Login URL of site: has mobile app? Yes/NO A working account: A description of what to capture exactly: [/code] [/align] [align=center]TOS You cannot Leak configs i sell you. You cannot resell them. i'll provide 1 day warranty for config. i can deny to create config for you at any point ChargeBack on PayPal leads to a Scam report. PS: i don't make config for site which has Recpatcha security by Google(Exception for BlackBullet Configs if you are ready to spend money for Captcha solvings). So please before contacting me check the site. There could be more reason for a config to not be possible. Payment Methods: Currenctly Accepting BTC,ETH, PayPal only F&F Can accept Gift cards too if its useful for me. Discord: Abdullah346#1295 [/align]
-
1 point
-
1 point[hide]matrixflame0@gmail.com:y0un00b00 mhp9411@hotmail.com:Cheetah12 meconium1337@gmail.com:herpderp123 tcowne92@gmail.com: DXTDG123 [/hide]
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointThanks for the share, i hope that is it up to date and the password are not changed by netflix
-
1 pointthanks brother u always give hq shit all the time :) +rep
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 pointthanks so much for the config
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point100k CPM? LMAO Okay I will see. I actually have never heard of this Fortnite checker. Edit: Got to love the console/cmd based checkers :D 2nd Edit: Nothing but retries.
-
1 point
-
1 point